Overboard: Kubernetes dashboard setup
In this tutorial we will setup the official Kubernetes Dashboard.
After installing the dashboard we will use Overboard to create a ServiceAccount and assign the necessary role. Then we will get an access token for that user.
Topics covered
- Dashboard
- Authentication and Authorization resources
Requirements
- A Kubernetes cluster to learn on such as Kubernetes on Docker or minikube.
- A basic knowledge of using kubectl
- Ingress enabled for your clusterW
- dotnet SDK installed
- Optionally, any IDE that supports F# (Visual Studio Code, IntelliJ Rider, Visual Studio, NeoVim)
Visual Studio Code with the Ionide is a great choice. See Setup your environment for more details.
Enable the Dashboard
To install the Dashboard into the kubernetes cluster you can run the following command. Check the GitHub repository for the latest version.
|
This creates about 14 different Kubernetes resources but the important ones for what we will be doing next are:
- A
Namespacecalled kubernetes-dashboard - A
ClusterRolecalled kubernetes-dashboard in the kubernetes-dashboardNamespace
You can navigate to your dashboard by going the the address http://localhost:8001/api/v1/namespaces/kubernetes-dashboard/services/https:kubernetes-dashboard:/proxy/.
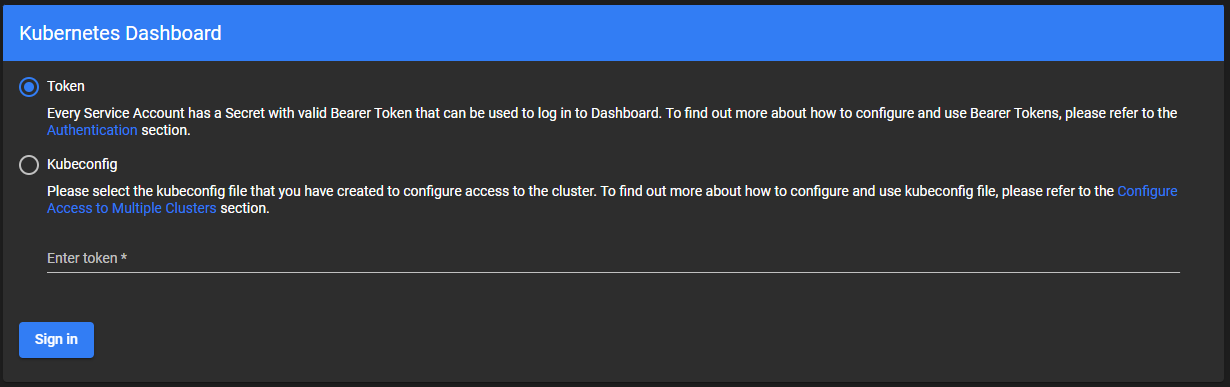
Remember to run proxy so you can access the cluster from your machine:
|
To login though, we need to create a ServiceAccount and connect the correct role to it. We will do this and then get a token.
Creating the Service Account
Next, we will create our fsx file and import the necessary packages and namespaces.
#r "nuget:Overboard"
// open the required namespaces
open System
open Overboard
open Overboard.Authentication
open Overboard.Authorization
Creating the ServiceAccount
The ServiceAccount is called admin-user and is in the kubernetes-dashboard Namespace.
This admin-user is only intended for testing on a local cluster! Use a more robust RBAC setup for a production setup.
let dashboardAccount = serviceAccount {
_name "admin-user"
_namespace "kubernetes-dashboard"
}
Assign role to ServiceAccount
As mentioned above, the ClusterRole kubernetes-dashboard is created when we install the dashboard. We need to connect it to the admin-user ServiceAccount.
We do this with a ClusterRoleBinding.
let dashboardRoleBinding = clusterRoleBinding {
_name "admin-user"
roleRef {
apiGroup "rbac.authorization.k8s.io"
kind "ClusterRole"
name "cluster-admin"
}
subject {
kind "ServiceAccount"
name "admin-user"
ns "kubernetes-dashboard"
}
}
Finally, we add this to a K8s config and write the results out to a dashboard.yaml file.
let dashboardConfig = k8s {
dashboardAccount
dashboardRoleBinding
}
let configDir = __SOURCE_DIRECTORY__
KubeCtlWriter.toYamlFile dashboardConfig $"{configDir}{IO.Path.DirectorySeparatorChar}dashboard.yaml"
Run the fsx file and then apply the config to your cluster you created to
|
Use the command for your terminal on your operating system to generate a token. Copying the token manually can cause issues (newlines etc.) so I recommend putting the token directly into your clipboard like shown below.
Windows cmd:
|
Powershell:
|
Mac:
|
Linux (with xclip installed):
|
Remember to start a proxy if you don't still have it running from earlier.
Don't copy/paste this command since the token is in your clipboard ;)
|
Now, navigate to the kubnernetes dashboard again, make sure Token is selected, and paste your token in the text field.
You should now have access to your cluster dashboard.
Congrats!
Conclusion
In this tutorial we saw how to easily install the Kubernetes dashboard and create a ServiceAccount and a ClusterRoleBinding to access it.
We used this ServiceAccount to access the dashboard with a generated token.
<summary> Name of the ServiceAccount. Name must be unique within a namespace. https://kubernetes.io/docs/reference/kubernetes-api/common-definitions/object-meta/#ObjectMeta </summary>
<summary> Namespace of the ServiceAccount. Namespace defines the space within which each name must be unique. Default is "default". https://kubernetes.io/docs/reference/kubernetes-api/common-definitions/object-meta/#ObjectMeta </summary>
<summary> Name of the ClusterRoleBinding. Name must be unique within a namespace. https://kubernetes.io/docs/reference/kubernetes-api/common-definitions/object-meta/#ObjectMeta </summary>